Arizona companies need to protect their networks and sensitive data and equip their “human firewall” against threats. As a regional provider of IT Managed Security Services and hosted private-cloud solutions, LeeShanok Network Solutions achieves success when our clients’ technology is secure, runs like a well-oiled machine, and supports their business operations without interruption.Every company is unique, and innovation comes into play when we design solutions using industry b est practices and a layered security model to cover all potential vulnerabilities. Our focus starts with training the users with best security practices, then providing reliable support necessary to keep all devices updated, and emerging vulnerabilities patched.
Documenting security policies and procedures helps an organization ensure all security layers are covered and guides staff on how to respond to security incidents. This documentation is often a requirement of compliance audits. At one of Arizona’s school districts, we assisted with formal documentation of their IT security policies and procedures and satisfied the auditor’s requirements.
Phishing attacks continue to be the top method for hackers to gain unauthorized access to company domains and valuable data. End-user security awareness training leads the pack in effective preparation and defense. A powerful feature of the training is to perform human verification when there is a request for confidential company information received in an email.
Many compliance and regulatory organizations require evidence of user training and testing for auditors to review. This data is collected from realistic phishing simulations and end-user training and documented with a Certificate of Completion. This meets the organization’s Continued Professional Education (CPE) requirements.

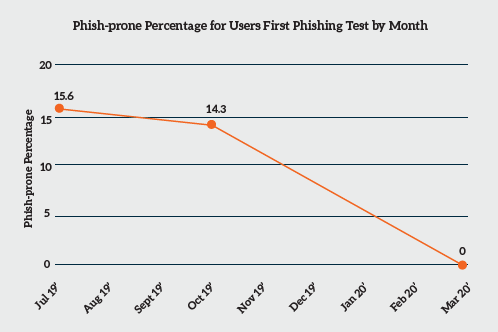
The average phish-prone percentage rate is a high 37.7% in the construction industry. LeeShanok has assisted many businesses achieve a near 0% phishing rate, as shown in the timeline graph.
Networks consist of multiple devices in several categories. All network devices run firmware and software, and patches released by manufacturers need to be identified and installed to continue their reliable operation and to protect against new exploits and vulnerabilities. We perform proactive routine tasks to investigate categories of our clients’ network devices and apply security patches.
Gateways and firewalls need configurations according to industry best practices to reliably protect against malicious traffic and risky content.
, 

LeeShanok’s team recommends geo-fencing that blocks traffic originating from specific high-risk geographical regions.
A well-oiled machine requires routine maintenance by specialized and experienced professionals to keep humming. LeeShanok’s innovation provides the repeatable processes and industry security best-practices that we live by every day as a team. This promotes proficiency and efficiency that provides our clients Peace of Mind with secure and reliable technology to operate their businesses.
For a confidential discussion of your cybersecurity strategy, the LeeShanok team is ready to assist!















